
Orolia GNSS simulators now support ultra-low latency of 5 ms
June 21, 2021
Latest advancement from Skydel uses software-defined advantages to deliver real-time performance Orolia has announced the launch of its […]
Read More

Latest advancement from Skydel uses software-defined advantages to deliver real-time performance Orolia has announced the launch of its […]
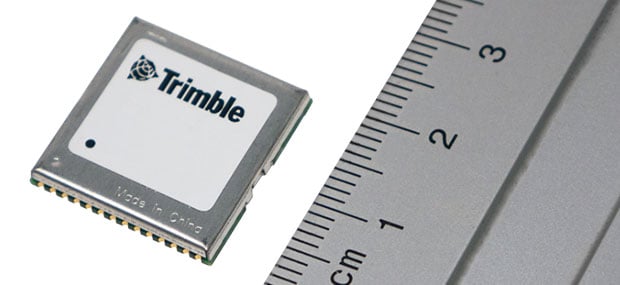
Dual-frequency timing module provides anti-jamming and anti-spoofing capabilities Trimble has introduced its first dual-frequency embedded timing module that […]

Microchip Technology has integrate its BlueSky technology signal-anomaly detection software into its SyncServer S600 Series network time server […]

The U.S. Department of Homeland Security (DHS) Science and Technology Directorate (S&T) has published the Positioning, Navigation, and […]

To mark the one-year anniversary of the PNT Executive Order, Orolia will host an interactive Coffee Talk webinar […]

In this second installment of our review of innovations in GNSS receivers, we present the responses from ComNav […]

What should the new administration’s priorities be to make PNT more resilient? We asked Brad Parkinson, the “Father […]
Follow Us